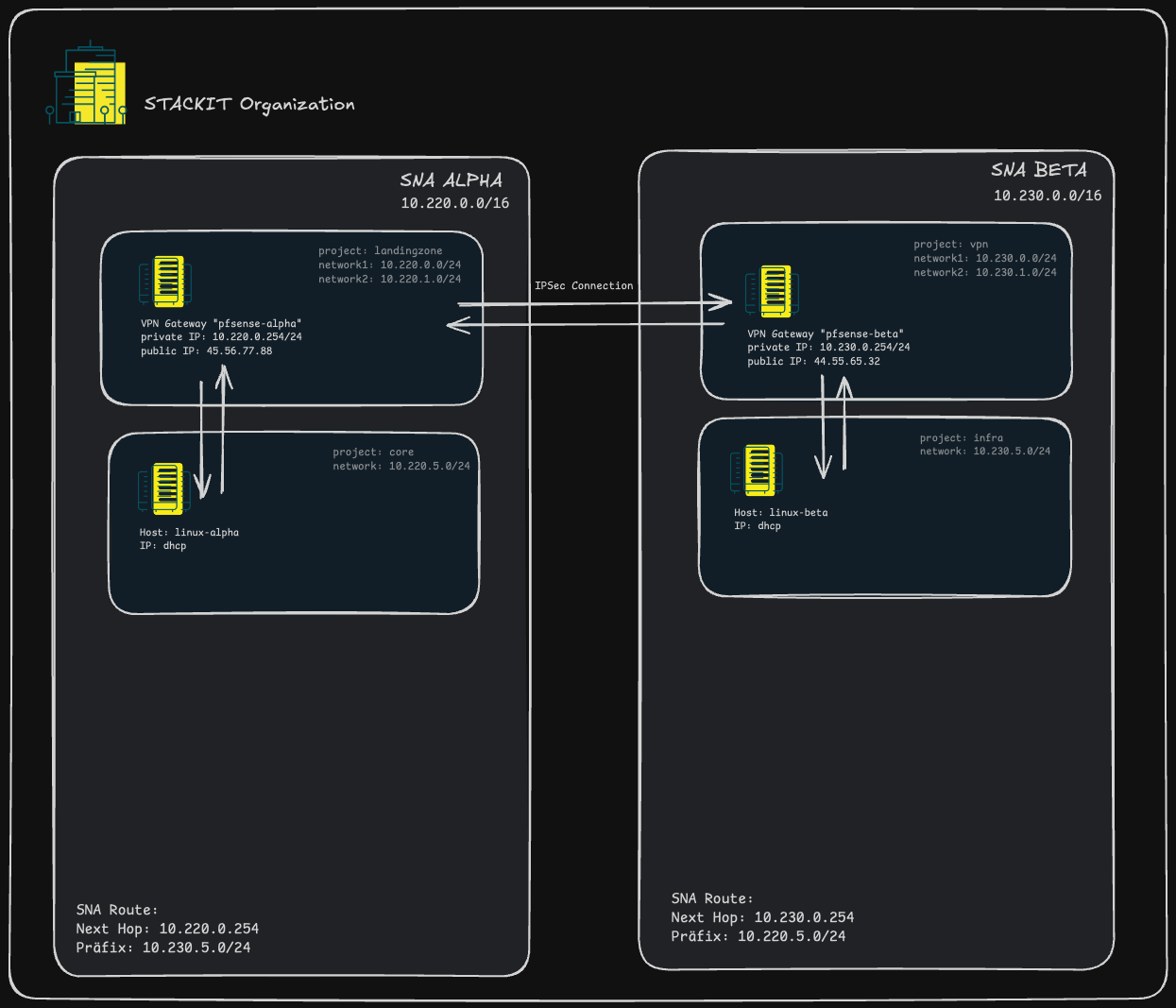
Same as the landinzone project with the difference that we create another SNA with a project and a pfsense for simulation a VPN IPSEC Connection.
| modules/project | ||
| .gitignore | ||
| 00-provider.tf | ||
| 01-network.tf | ||
| 02-pfSense-image.tf | ||
| 03-pfSense-appliance.tf | ||
| 04-attachment.tf | ||
| 05-server.tf | ||
| 06-security-group.tf | ||
| 07-object-storage.tf | ||
| 08-ske.tf | ||
| 80-keypair.tf | ||
| 99-variables.tf | ||
| landingzone_ipsec.png | ||
| modules.tf | ||
| README.md | ||
🌐 Infrastructure Deployment: Two SNAs with two Firewalls for showing VPN IPSEC Connections
This repository contains Terraform code to deploy the following sna/infrastructure projects:
📦 Projects Overview
1. ALPHA SNA
1.1 Landing Zone
- Deploys a single pfSense VM as the central firewall/router.
- Acts as the entry point for the environment.
- Configures WAN and one LAN network:
wan_network:10.220.0.0/24lan_network1:10.220.1.0/24
- Interfaces:
- WAN interface with static IP
10.220.0.254 - LAN interfaces with dynamic IP
- WAN interface with static IP
1.2 Core
- Deploys a single Virtual Machine (VM) for core services or testing purposes.
- Network setup includes:
p2_lan_network:10.220.5.0/24(routed)p2_wan_network:10.220.50.0/24(routed) - optional and deactivated
- Interfaces:
- LAN interface with optional configured security group
- WAN interface without additional security set
1.3 Backup
- Used for backup and disaster recovery scenarios.
- Creates an Object Storage Bucket.
- Relevant access credentials are provisioned for use with other services.
1.4 SKE
- Deploys a managed SKE (STACKIT Kubernetes Engine) cluster.
ske_network:10.220.10.0/24
2. BETA SNA
2.1 VPN
- Deploys a single pfSense VM as the central firewall/router.
- Acts as the entry point for the environment.
- Configures WAN and one LAN network:
wan_network:10.230.0.0/24lan_network1:10.230.1.0/24
- Interfaces:
- WAN interface with static IP
10.230.0.254 - LAN interfaces with dynamic IP
- WAN interface with static IP
2.2 Infra
- Deploys a single Virtual Machine (VM) for infra services or testing purposes.
- Network setup includes:
p6_lan_network:10.230.5.0/24(routed)
- Interfaces:
- LAN interface with optional configured security group and dynamic IP.
Overview
- The Project Backup and SKE is not shown in this picture. This will only show the flow of the connecting Networks via IPSec.
🚀 Getting Started
Prerequisites
- Terraform ≥ 1.3
- Valid STACKIT credentials
- Access to STACKIT APIs (IaaS, Kubernetes, Object Storage)
Deployment Steps
-
Clone this repository:
git clone https://professional-service.git.onstackit.cloud/professional-service-best-practices/landingzone_ipsec.git cd <repo-name> -
Initialize Terraform:
terraform init -
Review and adjust variables if needed:
99-variables.tf set organization id (also in project module) touch pfsense.qcow2 -
Plan and apply the configuration:
terraform apply
🔐 Output
The deployment will output:
- VM IP addresses
- pfSense Public IPs
- Kubernetes cluster information (kubeconfig)
- Object Storage credentials (access/secret key)
🔒 Make sure to store credentials securely and never commit them to version control.
📝 Notes
- This setup is optimized for a test or POC environment and is intended to setup an IPSEC Site2Site VPN.
- Check the SNA Routes for configuring the Remote Networks on pfSense side. Be sure to set the Identifier in IKE Phase 1 to the Public IP, because we are behind NAT.
- pfSense must be manually configured after deployment. (User: admin, Passwort: STACKIT123!)
- Kubernetes workloads are not included in this deployment but can be added later.
- LVM striping (RAID0) can be used for temporary IOPS/performance improvement — but requires attention to backups.
⚠️ Limitations
- The infrastructure is not auto-scaled or HA-enabled by default.
- No automated DNS or certificate management is configured.
📬 Support
For issues, please create a Ticket or contact professional-service@stackit.cloud
Author: Michael Sodan
License: MIT